VsFTP – Chiffrer les communications du serveur

Comme vu dans le précèdent article, concernant la mise en œuvre d’un serveur FTP. La communication par défaut n’est pas chiffrée.
Nous allons augmenter le niveau de sécurité de notre serveur FTP en y activant le chiffrement.
Ainsi, même si les données sont interceptées, elles ne pourront être lu sans la clef privée.
Avant tout, nous devons générer nos clefs privée et publique :
[pastacode lang= »bash » manual= »openssl%20req%20-new%20-newkey%20rsa%3A4096%20-x509%20-sha256%20-days%2090%20-nodes%20-out%20%2Fetc%2Fssl%2Fcerts%2Fvsftp_pub.crt%20-keyout%20%2Fetc%2Fssl%2Fcerts%2Fvsftp_priv.key » message= »Générer clefs » highlight= » » provider= »manual »/]
Ensuite fournir les informations demandé :
[pastacode lang= »markup » manual= »Generating%20a%204096%20bit%20RSA%20private%20key%0A………………………%2B%2B%0A………………………….%2B%2B%0Awriting%20new%20private%20key%20to%20’%2Fetc%2Fssl%2Fcerts%2Fvsftp_priv.key’%0A—–%0AYou%20are%20about%20to%20be%20asked%20to%20enter%20information%20that%20will%20be%20incorporated%0Ainto%20your%20certificate%20request.%0AWhat%20you%20are%20about%20to%20enter%20is%20what%20is%20called%20a%20Distinguished%20Name%20or%20a%20DN.%0AThere%20are%20quite%20a%20few%20fields%20but%20you%20can%20leave%20some%20blank%0AFor%20some%20fields%20there%20will%20be%20a%20default%20value%2C%0AIf%20you%20enter%20′.’%2C%20the%20field%20will%20be%20left%20blank.%0A—–%0ACountry%20Name%20(2%20letter%20code)%20%5BXX%5D%3A%20FR%0AState%20or%20Province%20Name%20(full%20name)%20%5B%5D%3AParis%0ALocality%20Name%20(eg%2C%20city)%20%5BDefault%20City%5D%3AParis%0AOrganization%20Name%20(eg%2C%20company)%20%5BDefault%20Company%20Ltd%5D%3Aelectrotuto%0AOrganizational%20Unit%20Name%20(eg%2C%20section)%20%5B%5D%3AIT%0ACommon%20Name%20(eg%2C%20your%20name%20or%20your%20server’s%20hostname)%20%5B%5D%3A192.168.56.106%0AEmail%20Address%20%5B%5D%3Aadmin%40electrotuto.com » message= » » highlight= » » provider= »manual »/]
La ligne la plus importante c’est COMMON NAME, dans notre cas on met un IP mais la bonne pratique serait de mettre un FQDN. exemple FTP.electrotuto.com
Modifier le fichier de configuration comme cela :
[pastacode lang= »bash » manual= »%23%20Ceci%20configure%20vsFTPd%20en%20mode%20%22standalone%22%0A%23listen%3DYES%20%20%20%20%0A%23listen_ipv6%3DNO%0A%0A%23%20On%20d%C3%A9sactive%20les%20connexions%20anonymes%0A%23%20et%20on%20active%20les%20non-anonymes%20(c’est%20le%20cas%20des%20utilisateurs%20virtuels)%0Aanonymous_enable%3DNO%0Alocal_enable%3DYES%0A%0A%23Pour%20permettre%20%C3%A0%20vos%20utilisateurs%20locaux%20(ceux%20qui%20ont%20un%20compte%20sur%20la%20machine)%20de%20se%20connecter%20au%20serveur%20et%20d’%C3%A9crire.%20%0Awrite_enable%3DYES%0A%0A%23%20permet%20de%20d%C3%A9finir%20les%20droits%20par%20d%C3%A9faut%20lors%20de%20creation%20de%20fichier%20et%20r%C3%A9pertoire%0Alocal_umask%3D022%0A%0A%23%20Pour%20des%20raisons%20de%20s%C3%A9curit%C3%A9%20on%20interdit%20toute%20action%20d’%C3%A9criture%3A%0A%23les%20anonymes%20n’ont%20pas%20le%20droit%20de%20charger%20des%20fichiers%20sur%20le%20serveur%0Aanon_upload_enable%3DNO%0A%0A%23les%20anonymes%20n’ont%20pas%20le%20droit%20de%20cr%C3%A9er%20de%20r%C3%A9pertoire%0Aanon_mkdir_write_enable%3DNO%0A%0A%23%20message%20affich%C3%A9%20aux%20utilisateurs%20s’ils%20vont%20dans%20un%20certain%20r%C3%A9pertoire%20%0Adirmessage_enable%3DYES%0A%0A%23cette%20option%20est%20activ%C3%A9e%2C%20vsf%20affichera%20les%20listes%20des%20r%C3%A9pertoires%20avec%20l’heure%20de%20votre%20fuseau%20horaire%20local.%0Ause_localtime%3DYES%0A%0A%23active%20les%20logs%20lors%20de%20chargement%20ou%20t%C3%A9l%C3%A9chargement.%0Axferlog_enable%3DYES%0A%0A%23confirme%20que%20le%20port%20ftp%20est%20le%2020%0Aconnect_from_port_20%3DYES%0A%0A%0A%0A%23destination%20du%20fichier%20de%20logsd%0Axferlog_file%3D%2Fvar%2Flog%2Fvsftpd.log%0A%0A%23%20Gestion%20des%20temps%20de%20connexion%0Aidle_session_timeout%3D600%0Adata_connection_timeout%3D120%0Aconnect_timeout%3D60%0Aaccept_timeout%3D60%0A%0A%23activez%20cette%20option%20et%20le%20serveur%20reconna%C3%AEtra%20les%20requ%C3%AAtes%20ABOR%20asynchrones.%0Aasync_abor_enable%3DYES%0A%23%20mode%20ASCII%20non%20activ%C3%A9%0Aascii_upload_enable%3DNO%0Aascii_download_enable%3DNO%0A%0A%23banni%C3%A8re%20de%20bienvenu%20lors%20de%20l’identification%0Aftpd_banner%3DBienvenue%20sur%20le%20serveur%20FTP%20de%20BOOKTIC%0A%0A%23%20On%20veut%20que%20les%20utilisateurs%20virtuels%20restent%20chez%20eux%3A%20’%2Fhome%2Fftp%2F’%0Achroot_local_user%3DYES%0A%0A%23%20ne%20pas%20emprisonner%20dans%20son%20r%C3%A9pertoire%20home%20les%20utilisateurs%0Achroot_list_enable%3DNO%0A%0A%23%20Les%20prisonniers%20peuvent%20%C3%A9crire%20dans%20leur%20propre%20r%C3%A9pertoire%20%20%20%20%0Aallow_writeable_chroot%3DYES%0A%0Asecure_chroot_dir%3D%2Fvar%2Frun%2Fvsftpd%0A%0A%23%20Cette%20cha%C3%AEne%20est%20le%20nom%20du%20service%20PAM%20que%20vsftpd%20utilisera.%0Apam_service_name%3Dvsftpd%0A%23%20Cette%20option%20sp%C3%A9cifie%20l’emplacement%20du%20certificat%20RSA%20%C3%A0%20utiliser%20pour%20SSL.%0Arsa_cert_file%3D%2Fetc%2Fssl%2Fcerts%2Fvsftp_pub.crt%0Arsa_private_key_file%3D%2Fetc%2Fssl%2Fcerts%2Fvsftp_priv.key%0Assl_enable%3DYES%0A%0A%23%20Pour%20des%20raisons%20de%20s%C3%A9curit%C3%A9%20on%20interdit%20toute%20action%20d’%C3%A9criture%3A%0Aanon_other_write_enable%3DNO%0A%0A%23%20on%20souhaite%20la%20lecture%20seule%20%0Aanon_world_readable_only%3DYES%0A%0A%0A%0A%23chemin%20du%20r%C3%A9pertoire%20anonyme%0Aanon_root%3D%2Fsrv%2Fftp%2Fanon » message= » » highlight= » » provider= »manual »/]
Relancer le service VsFTPD
[pastacode lang= »bash » manual= »systemctl%20restart%20vsftpd » message= » » highlight= » » provider= »manual »/]
Maintenant essayons de nous y connecter avec FileZilla :
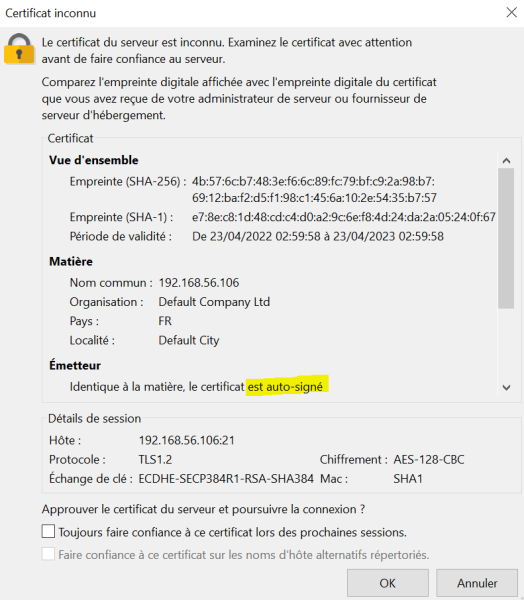
On aura un message d’alerte nous indiquant que le certificat n’est pas reconnue. En effet, c’est un certificat que nous avons généré nous même. il n’est pas fournit par une autorité de certification reconnue et que Filezilla a le CA dans son trousseau.
Accepter le message…
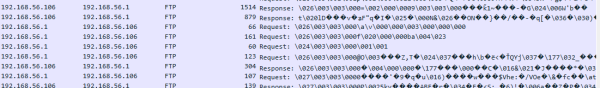
Maintenant notre capture wireshark nous montre que tout est illisible. Car bien évidement tout est chiffré.
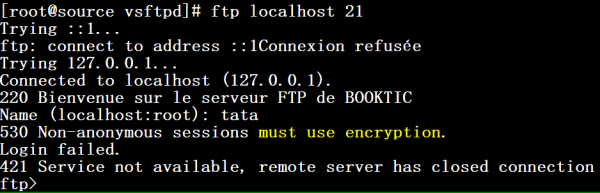
Lorsqu’on souhaite initié une connexion via CLI on est rejeté :
PS : En cas de problème, vérifier votre firewall, et SElinux.